Healthcare Information System Technique Analysis
Main Article Content
Abstract
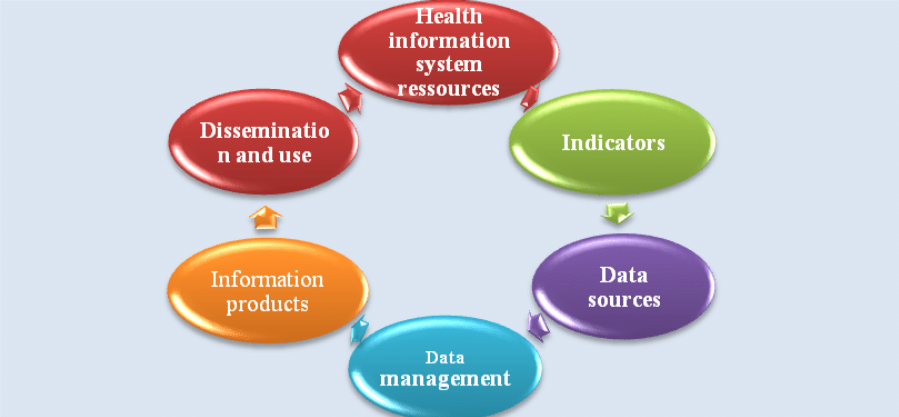
Healthcare information system methods refer to specific frameworks applied in computer systems to dictate users’ accessibility to specific objects. In this case, it is the strategy applied in limiting access to the computers virtual, physical, and system resources. It is also the process by which users gain privileges and are granted access to information, resources, and systems. To facilitate this process and assure access, users must present specific credentials and details that are verified to corroborate the user’s identity; thereby ensuring security. For instance, a username and login password can act as a healthcare information system, granting a user access to a secured computer system. However, this option does not guarantee security because the credentials can be transferred to another user. A more secure system could include a thumbprint or retinal scanner that is unique to specific users and, cannot be transferred. In this respect, healthcare information system can be construed as a strategy for securing computers by supporting authorization, authentication, and auditing processes that identify the user seeking access to the system. As such, healthcare information system is a practice responsible for securing information and setting privileges towards the identification of a specific user, listing sites that can be accessed, and the time when access is allowed. Notably, the entire security system is offered by administrators. This study proposed a hybrid healthcare information system technique to discern its efficiency, as well as future implications for the field of healthcare systems.